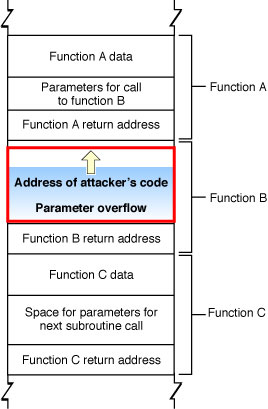
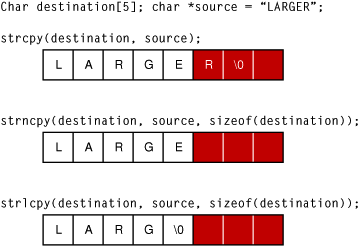
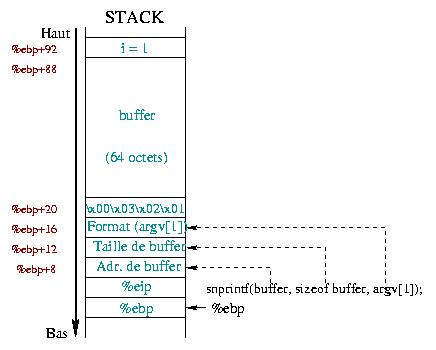
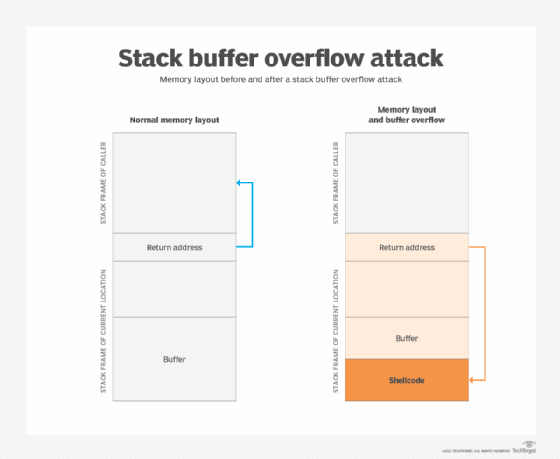
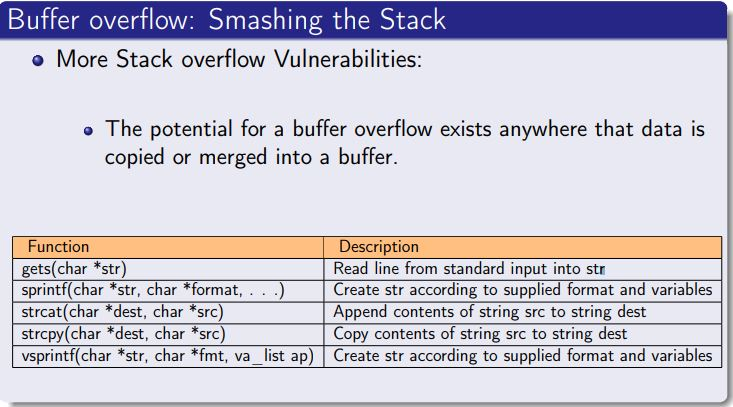
Applied Sciences | Free Full-Text | An In-Depth Survey of Bypassing Buffer Overflow Mitigation Techniques
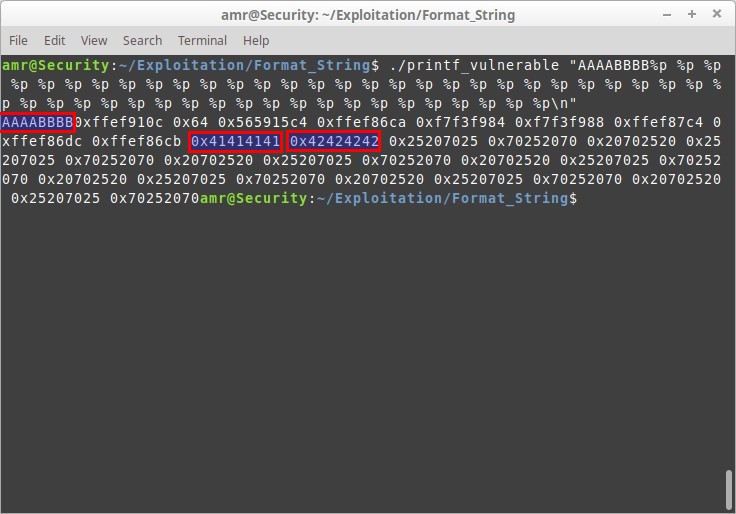
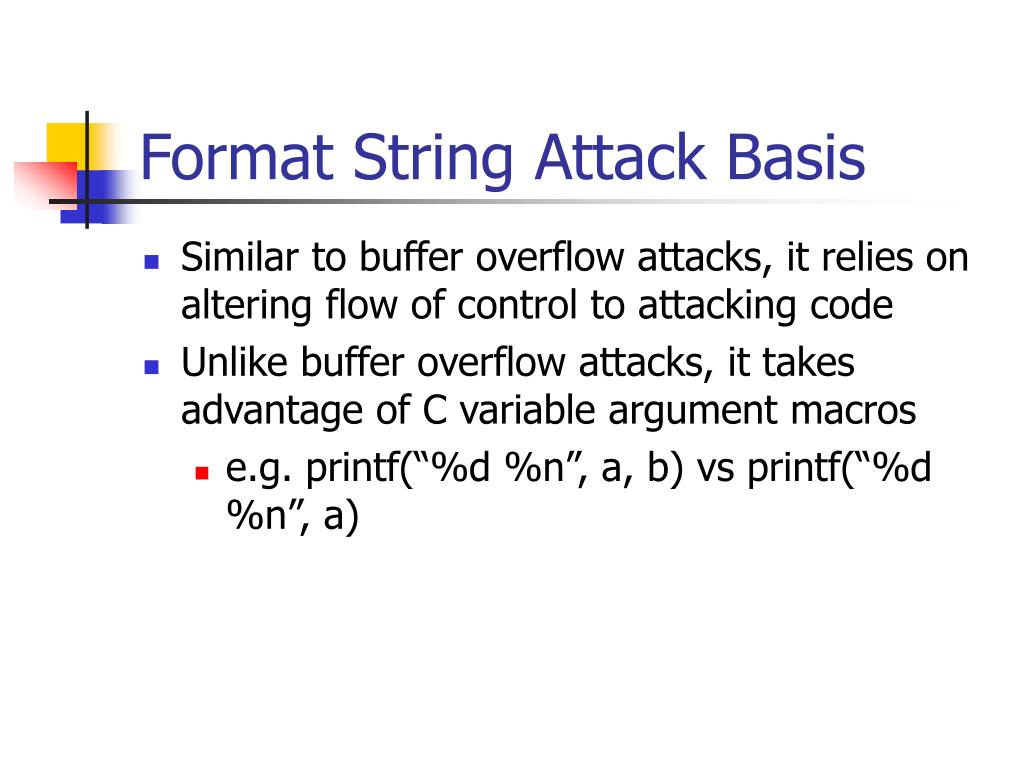
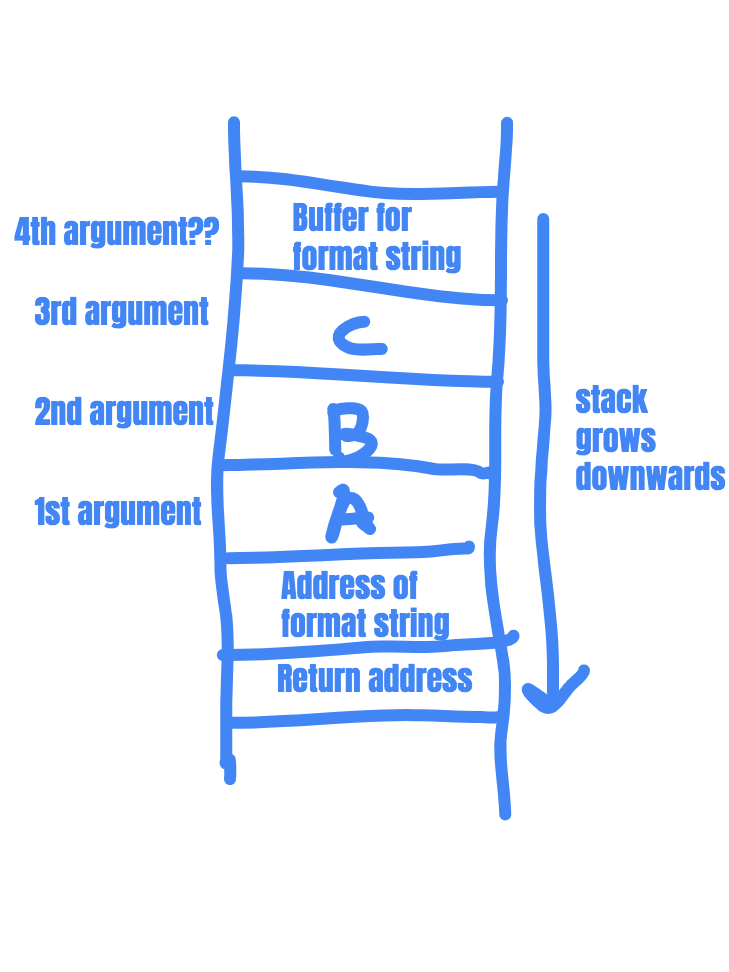
Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother « Null Byte :: WonderHowTo

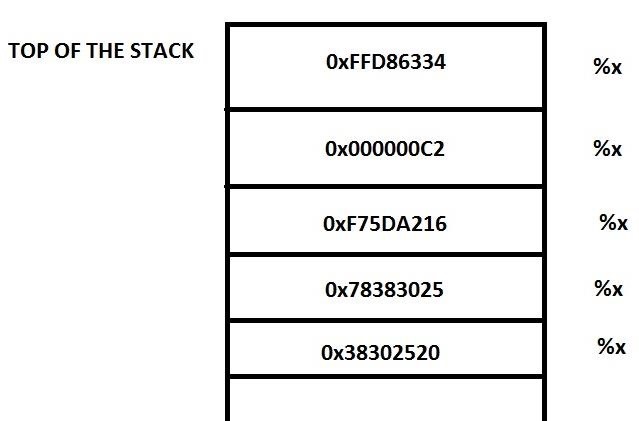
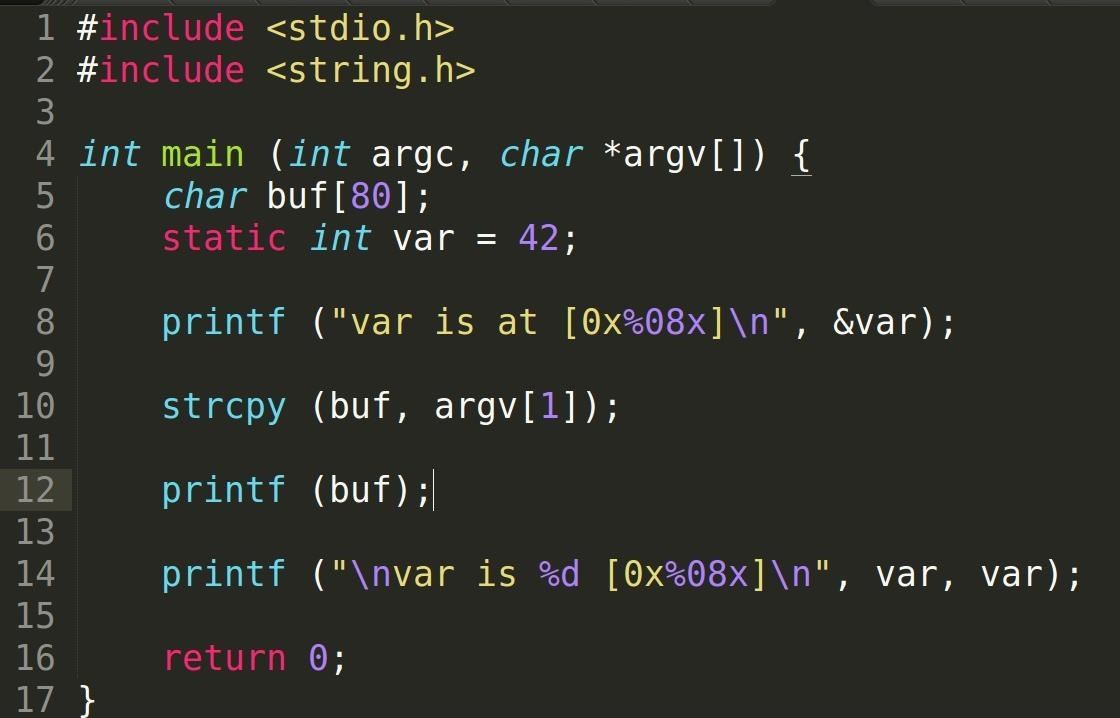
Killer Queen CTF : Tweety Birb (Canary bypass with format string vulnerability) | by Hariharan@Blog:~$ | Medium